Continuing to formalize channels between distinct marketplace actors, governments, and law enforcements, although however maintaining the decentralized nature of copyright, would advance speedier incident reaction as well as boost incident preparedness.
Many argue that regulation successful for securing banking institutions is considerably less productive from the copyright House due to the industry?�s decentralized mother nature. copyright requires extra stability restrictions, but In addition it requires new alternatives that bear in mind its discrepancies from fiat money institutions.,??cybersecurity steps may possibly grow to be an afterthought, especially when companies deficiency the money or staff for these types of actions. The trouble isn?�t distinctive to Those people new to enterprise; however, even effectively-recognized companies may well Allow cybersecurity drop towards the wayside or may absence the education to be familiar with the speedily evolving threat landscape.
copyright.US is not really to blame for any loss you could incur from rate fluctuations once you buy, provide, or hold cryptocurrencies. You should make reference to our Phrases of Use For more info.
Bitcoin takes advantage of the Unspent Transaction Output (UTXO) product, similar to transactions with Actual physical income the place Each and every person Monthly bill would want for being traced. On other hand, Ethereum utilizes an account product, akin to your bank account with a functioning stability, that is extra centralized than Bitcoin.
Even so, matters get difficult when just one considers that in the United States and most international locations, copyright remains largely unregulated, along with the efficacy of its present-day regulation is often debated.
These danger actors were then in a position to steal AWS session tokens, the short term keys that permit you to ask for momentary qualifications on your employer?�s AWS account. By hijacking Lively tokens, the attackers were being able to bypass MFA controls and gain access to Secure Wallet ?�s AWS account. By timing their efforts to coincide Using the developer?�s typical perform hours, here they also remained undetected till the actual heist.
 Jonathan Taylor Thomas Then & Now!
Jonathan Taylor Thomas Then & Now! Luke Perry Then & Now!
Luke Perry Then & Now! Rick Moranis Then & Now!
Rick Moranis Then & Now!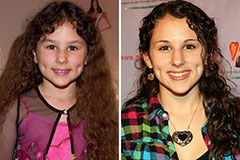 Hallie Eisenberg Then & Now!
Hallie Eisenberg Then & Now! Lynda Carter Then & Now!
Lynda Carter Then & Now!